Overview
In the current era of rapid digital advancement, the security and efficiency of data transmission have become crucial elements for the stable operation of various applications. Peer-to-Peer (P2P) technology has emerged as a cutting-edge solution, aiming to establish a robust and reliable communication link between communication endpoints.
Glossary
Endpoint: Refers to either party in a P2P communication link. It can be the EVVR App, EVVR OS, etc.
E2EE: End-to-end encryption.
Signaling Server: In a communication system, especially in real-time communication systems such as VoIP, video conferencing, and instant messaging, it is a server used to transmit control information. It is primarily responsible for coordinating various signaling messages during the communication process. These signaling messages do not contain actual media data (such as voice and video content), but are used for operations such as establishing, managing, and tearing down communication connections.
UDP: User Datagram Protocol. It is a simple transport – layer protocol.
UDP Hole Punching: UDP hole punching is a method for implementing NAT traversal, allowing the establishment of a two-way UDP connection between Internet hosts located in private networks using NAT.
DTLS: Datagram Transport Layer Security. It is a protocol for securing datagram-based communication.
NAT: Network Address Translation. It is a technology in IP networks used to convert one IP address space into another. Its main purpose is to solve the problem of IP address shortage and provide a certain degree of network security protection.
NAT Routing: It is a technology that combines the Network Address Translation (NAT) function with the routing function. It not only forwards data packets between different networks (routing function), but also converts the source IP address and port number or the destination IP address and port number in the data packets during the forwarding process (NAT function), enabling hosts in different network address spaces to communicate with each other.
Principle
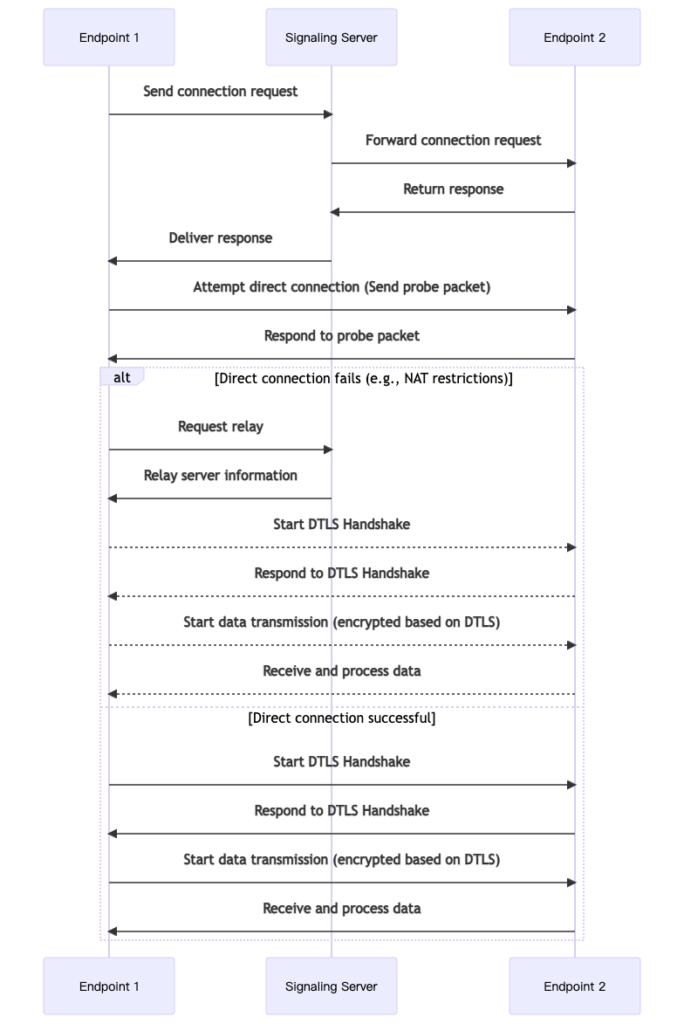
In the P2P communication scenario, the P2P architecture was designed to prioritize end-to-end direct communication from the outset. This is aimed at maximizing communication efficiency, reducing latency, and ensuring the autonomy and security of data transmission. When one endpoint plans to initiate a connection request, it first interacts with the signaling server. After receiving the request, the signaling server verifies the identity of the initiator. Once the identity is confirmed, it assists in accurately forwarding the connection request to the endpoint to be connected. Subsequently, upon receiving the request, the endpoint to be connected generates a response and, relying on the signaling server, sends this response back to the initiating endpoint. At this point, both endpoints start the network connection probing process to find a suitable connection path to establish a connection.
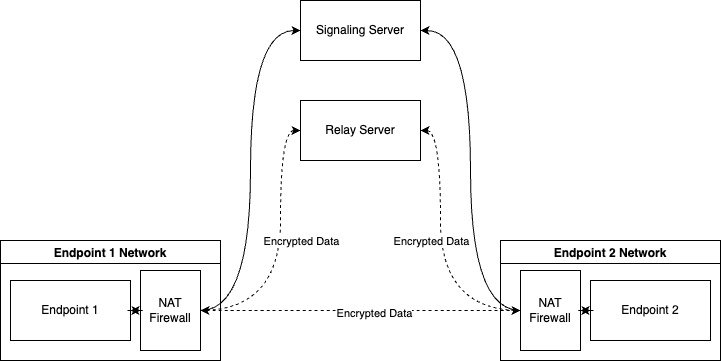
However, the real-world network environment is complex. In some cases where direct connections cannot be established, such as being restricted by NAT routing or due to other network issues like network congestion or firewall interference, P2P can adapt flexibly and use the server to relay data to ensure normal communication. It is worth emphasizing that, in this process, the E2EE technology based on DTLS plays a crucial role. DTLS can encrypt the data transmitted between endpoints. From the moment the data leaves the sending endpoint, it is transformed into ciphertext using an encryption algorithm. The ciphertext is then sent to the receiving endpoint along the established transmission link. Due to this encryption mechanism, even if the server is involved in relaying the data, it cannot obtain the decryption key and thus has no way of knowing the specific content of the communication. Therefore, even in the face of the dilemma of not being able to establish a direct connection, the privacy and security of communication are still firmly guaranteed.
Architecture Diagram
Sequence Diagram